Top 5 Security Concerns For Small Businesses

Sixty percent of small businesses close within six months after a cyber-attack. That statistic comes from Rep. Chris Collins (R-NY), ...
Read more
6 Basic Things To Become A Good Hacker

Hacking had never been an easy work. Never! But still a lot of computer freaks want to be a hacker. ...
Read more
Email and Internet Security [Simple Guide]

A computer user has to be aware of the incredible dangers lurking on the internet. Here are the two computer ...
Read more
Simple Tips To Secure Your Facebook Account

Getting Hacked is a nightmare! Especially if your Facebook account is hacked then it is worst of all. As a ...
Read more
HOW TO: Update WordPress Secret Keys
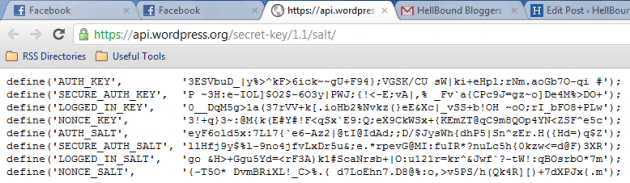
WordPress Secret Keys are kinda similar to passwords, harder the better. Which is tough to crack? This one “3gFi67dfads8FnU9” or ...
Read more
7 Best Tips To Keep Your Gmail Account Secure

Gmail is one of the most popular and user-friendly web based email on the Internet, and therefore the safety of ...
Read more
Is Your Password Hackable? [INFOGRAPHIC]
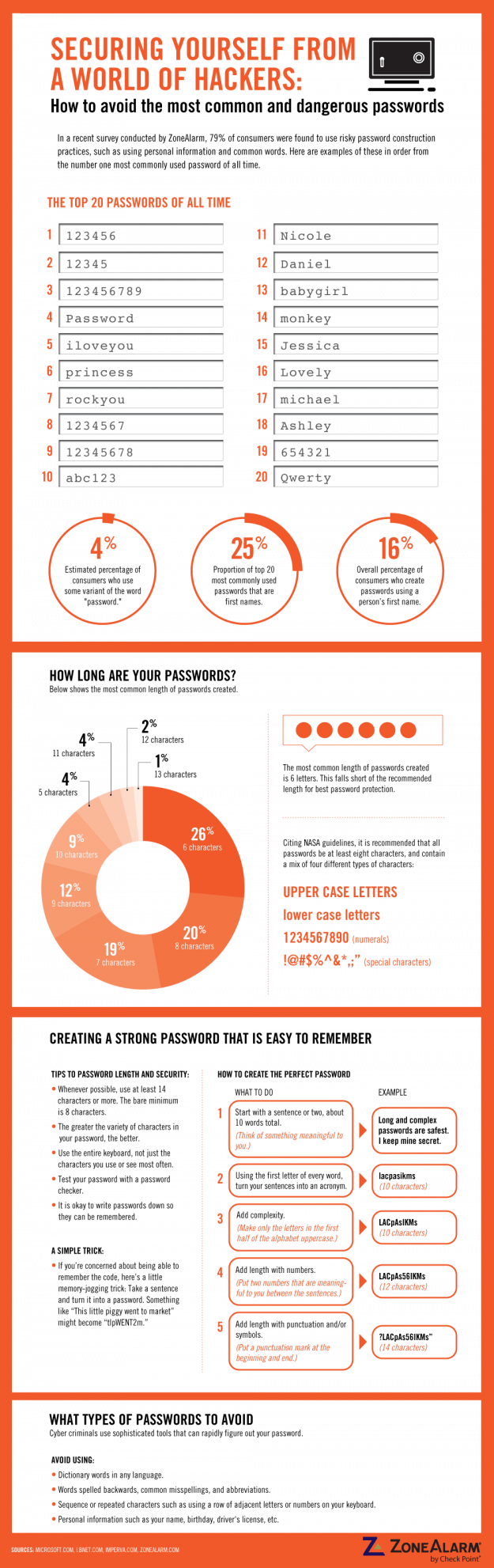
Ask any expert a security tip, I bet the first tip would be ‘keep strong password’. Nothing replaces strong password. ...
Read more
Securing WiFi Connection – Basic Things

The benefits of the Internet are well known and people are now owning more than a single computer connected to ...
Read more
Security Concern In United States [INFOGRAPHIC]
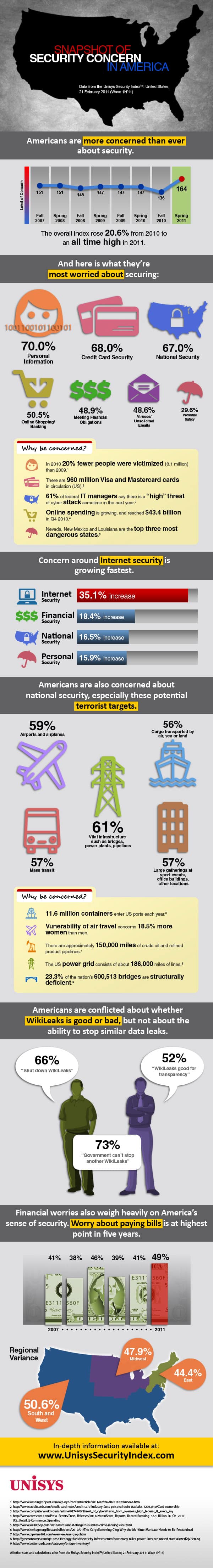
According to Unisys, identity theft is a leading concern of Americans, with seven of ten US citizens seriously concerned about ...
Read more
HOW TO: Prevent Facebook Friends To Post On Your Wall
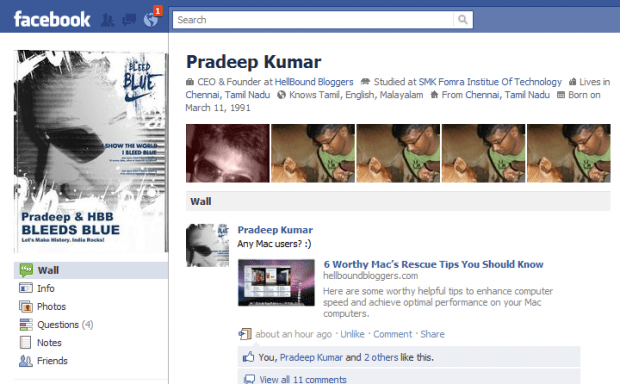
Everyday I used to get freaking SPAM wall posts, and seriously deleting them one by one annoys me a lot! ...
Read more