Labnol: Our Theories On What Happened

Labnol, (or Digital Inspiration) and all of Amit’s blogs and websites were recently taken down by hackers (Fortunately, they’re back ...
Read more
European Space Agency (ESA) Website Hacked!

A hacker reportedly compromised ESA, opening up sensitive project logs and exposing hundreds of email addresses and passwords associated with ...
Read more
GoDaddy WordPress Blogs Infected With Malware [Alert]
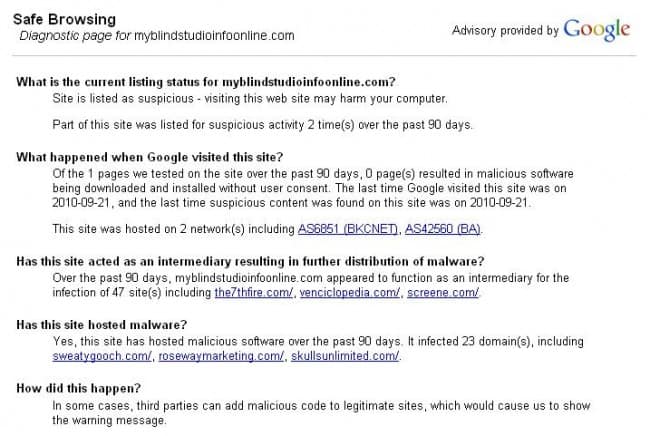
Majority of WordPress blogs hosted on GoDaddy were infected with some kind of malware for the past few days. Just ...
Read more