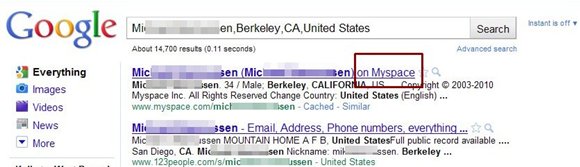
Email and Internet Security [Simple Guide]

A computer user has to be aware of the incredible dangers lurking on the internet. Here are the two computer ...
Read more
Explode Your E-Mail List With Pre-Filled Subscription Form

You all probably know that it’s important to build a list (of e-mails that is). Well, I’ve had an interesting idea. ...
Read more
Get Through Your Email Faster – Gmail Priority Inbox
Yes, now you can get through your email faster than ever. Priority Inbox, a new feature from Gmail, automatically identifies ...
Read more
8 Real Reasons To Subscribe To Our Blog

Well, read the title. Read? Read it once again. 8 Real Reasons To Subscribe To Our Blog. This is Our ...
Read more
Create Safe & Secure Email Address For Your Children

Most of the parents are worried about the negative side of Internet i.e., the Dark side. Children can get addicted ...
Read more