An information from scratch can be used to gather certain information that can be really astonishing. Here in this post I will show you how a person can reach your place if he/she has your IP address or domain name. Here I will demonstrate using a spam email which deliberately flooded my inbox from a particular sender and show you how we can reach his house. So lets start….
Disclaimer: This post is actually to aware people about there online privacy rather misuse this trick.
Information Gathering :
- From the email I got the “Domain Name” and name of the person and used it do the whois. As you all can see I got the address, phone no, fax etc from the image below. You can also use the IP address from the email header to obtain the information.
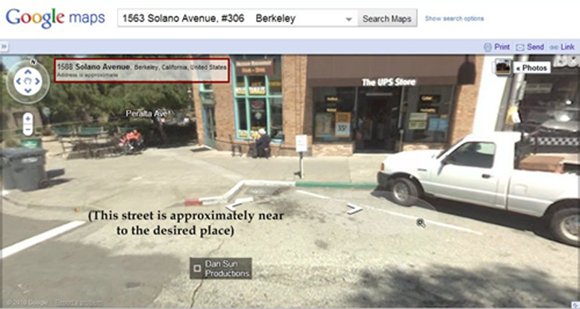
- Then I opened Google Maps to find the street view of the above obtained address. As you all can see I reached the street of the person and the desired place is approximately near to it.
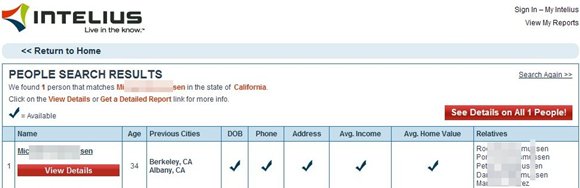
- I will show you what more info I got, I used his name,city and country to find info about his family from here as shown below.
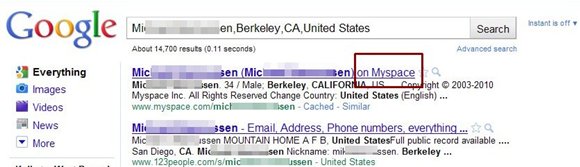
- Then using his name and location in Google search I found his MySpace account as shown below and got to see his face.
Countermeasures:
#1 – One should always use “Tor” like anonymous tools while browsing and especially using email accounts.
#2 – Keep the information of your Domain name set to private.
#3 – Keep the information on your Social Networking sites set to private.
#4 – Take care while sharing your Phone no or Fax no with any stranger or unknown website.
This guest article is written by Satyajit Das, Author and Owner of SecurityHunk. He is a 23 years old ethical hacking enthusiast and a part time blogger. If you wish to write for us, kindly check this.










Well, the country level domain can't be set for private registration …so their respective address are open to all just, in the name of nation's security 🙁
When we register domain we are required to provide basic information about add, phone no, and email ids. But, after that how can we change or make it private, so that it will not be visible to others?
Hacking is a very bad act
This is quite surprising
This sound scary but what can the hacker do even if he reaches my home?
This is scary!
Hi satyajit, I think you have great knowledge on hacking. Good work.
Can you identify frm which place this comment has come. ha..ha..
Hi satyajit, I think you have great knowledge on having. Good work.
Can you identify frm which place this comment has come. ha..ha..
First I would like to thank for your comment 🙂
One thing you should not forget when you comment using a unmasked Ipaddress on this blog or many other then the commenter’s Ipaddress is noted…hehehe….so i feel you have got the answer to your query… lol 😀
it’s a smart idea to set domain privacy to private. As prevention is better than cure.
yes certainly Isha …many people tend to neglect that and end up in unrecoverable situation… 🙂
Thanks… 🙂
Its really great you have shared it here. I really traced one of my friends blackmailer suing this method. Though I extracted the IP using a demo website which logged his ip when he visited it..:D
It can be done in many ways…here i have tried to show the readers with a simple example… 🙂 it can be done more extensively….and can give more scary outcomes…which may be out of expectation…… 🙂
Thanks… 🙂
Hello Satyajit,
Indeed, very intelligent tricks for finding out someone’s identity. But also, this kind of stuff isn’t ok at all, the privacy is violated through information leaks, these social network websites are way too insecure and you can easily be found, with the name and the email address/telephone number you can find out everything about someone’s identity, almost everything. I recommend setting the privacy level very high, try to anticipate this kind of things, these leaks of information can be very dangerous and you can risk to be black-mailed in some cases by ‘the bad guys’. So it is better to keep your identity as hidden as possible, especially on the social network websites, where ANYONE can see your name and details about your life + pictures, it’s way too dangerous and useless, you never know what could happen so it’s better to be cautious. Keep up the good work, excellent article, good informations, I hope the people will start being more attentive with their privacy.
Best regards,
Maria
Privacy is of foremost importance to each and every person…. 🙂 few simple tweaks can help it attain… 🙂 so stay safe…
Thanks 🙂
never expected such a post here
awesome 🙂
Hi Satyajit,
Very informative post and I really don’t have idea about it. Now I’ll be more careful. Thanks for sharing your experience.
Thanks that you liked it… 🙂
Nice post mate ! but i dont think google maps such clear and crisp images for India ( i mean he wont get clear view of the house) but still address is enough to catch us ! Should stay safe
I guess its google street view…
@Anubhab yes its the google street view… 🙂
Thanks 🙂
I never know this can be done, lol. Good one Satya
Thanks Praveen 🙂
Privacy should be maintained.
Its a way too risky, hope I may never become their target 😀
Nice! Thanks for the share Satyajith! Really appreciate infos like these!
Hackers are smart guys, who never comes your place but actually hack your PC only
Yeah Hackers are certainly smart and innovative too…:) yeah i agree hacker can break into your box…but that is not the only thing…. 😀
Thanks 🙂
Clever guy.
I like it.
Challenging you to discover me. He He He
lol 😀 surely keep your door open.. 🙂
Thanks that you liked it.
What if the other person uses gmail or other email service for sending spam mails? Then this trick will be of no help.
Yeah that can be a void attempt in that case to some extent but as you can see here i have used the domain name….rather than the Ipaddress…. 🙂 for example your domain name is “theitechblog.com” i may do the “whois” and then proceed… 🙂
I have shown a simple example by picking an email from the spam…it can be more scary…if done in an elite way…. 😀
Thanks 🙂
Hey thanks for the information,I will change privacy setting.
Thanks a lot that you liked the post… 🙂
Great article Satyajit. I think social media has made hacking and getting personal information of people even more easier than ever before. It is really important that one should be pretty aware while revealing personal information in the internet or web.
Yeah Shiva….many people forget about there privacy settings but few simple tweaks can really save them a big mishap…. 🙂
Thanks 🙂
Important Article first off. Whois protection is something you gonna be looking into seriously. Because nowadays people the Internet well enough & even a novice can find out certain basic info abt u.
Yeah I completely agree with you , everyone need to aware of this and do not lay there private info open to everyone….
Thanks 🙂
Nice post satyajit really interesting to read 😀 loved it and yes this is how we’re exposing our info. on internet ? 😮
Thanks…. 🙂
this is the First Step in Hacking called Reconissance and next leads to Social Engineering…Nice Share Satyajit…
This method is actually called as “DOXING” I have shown a simple example by picking an email from the spam…it can be more scary…if done in an elite way…. 🙂
Thanks… 🙂
I hope no one comes to my place 😉 Nice find Satyajit… 🙂
All you need is mask you privacy as much you can ….and keep away the online criminals to ring your house bell…. 😀
Thanks 🙂